North Korean Cyber Threat Actors
Prior to the announcement of the most recent Trump-Kim “nuclear” summit, Vice President Mike Pence met with Kim Yong Chol in January. This was Kim’s second visit to the US in under a year, and he has been one of the chief aides during the recent denuclearization talks holding the office of Vice Chair of the Central Committee of the Worker’s Party of Korea.
Kim Yong Chol was the Director of the Ministry of the People’s Armed Forces Reconnaissance Bureau and the Director of the Reconnaissance General Bureau (정찰총국) from its formation in 2009 until 2016. During that time, Kim oversaw the 2010 sinking of the Cheonan and the Yeonpyeong-Do shelling that same year. The RGB maintained control of most DPRK cyber capabilities under the 121st Unit.
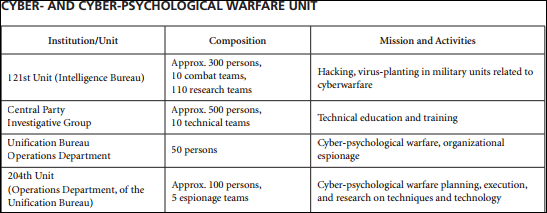
121st Unit | Lazarus Group
The 121st Unit is likely responsible for the Sony Pictures hack attributed to the “Lazarus Group”, “Hidden Cobra”, and “Guardians of Peace.” This group contains two sub-groups termed “Andariel” and “Bluenoroff.” Collectively, these groups have launched cyberattacks on organizations around the world, with “Bluenoroff” focusing on financial institutions and “Andariel” focusing on ROK targets. Below is a timeline of attacks attributed to the group from Operation Flame in 2007 to the WannaCry attacks in 2017.
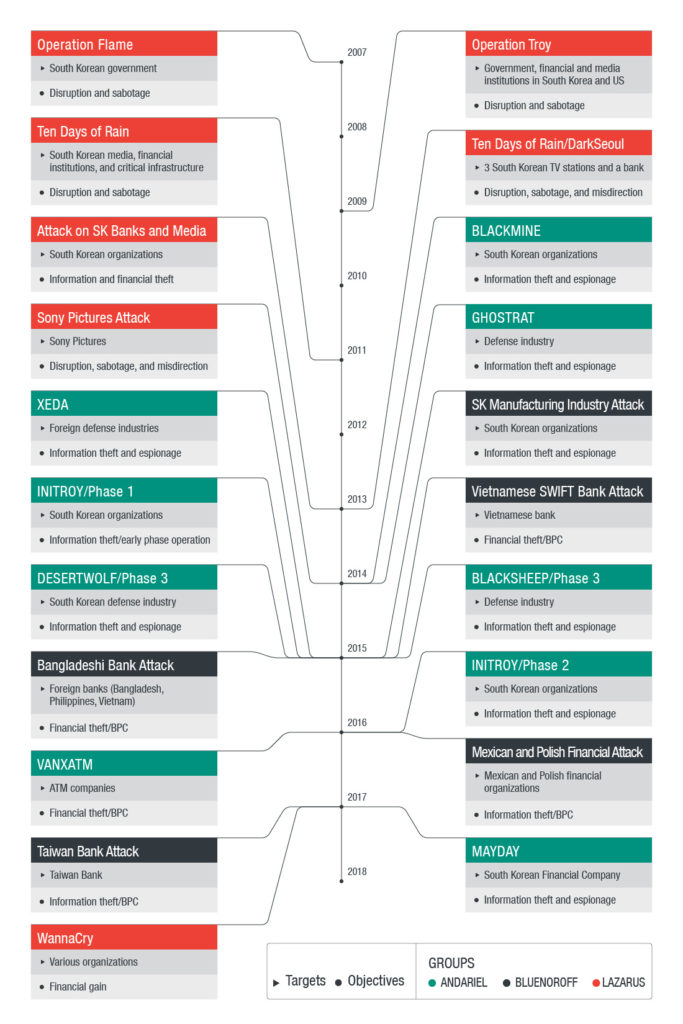
Some malware samples associated with the Lazarus Group’s attacks on financial institutions used transliterated Russian words in communications with the C2 server. However, the Russian words used indicate the developers are not native Russian speakers.
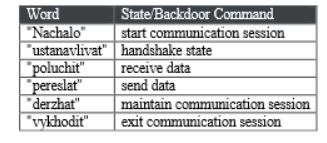
Additionally, the samples analyzed in this report are based on cURL, allowing for file transfer over multiple networking protocols using SSL/TLS. Client URL (cURL) is a command-line tool providing file transfer functionality using generic Uniform Resource Identifier (URI) syntax. Further, malware samples used by the Lazarus Group have included: KILLMBR.E, QDDOS, and Destover (Used in the Sony Pictures and South Korean financial institutions hacks).
APT 37 (REAPER) | Group 123 and ScarCruft
According to FireEye, DPRK-based APT 37 is also known as Group 123 and ScarCruft. The group’s activities have been attributed to the DPRK based on targets aligned with DPRK interests, malware code compilation times coinciding with local working hours, and an accidental self-infection of malware revealing the developer’s IP address. Malware samples associated with APT37 are: CORALDECK, DOGCALL, GELCAPSULE, HAPPYWORK, KARAE, MILKDROP, POORAIM, RICECURRY, RUHAPPY, SHUTTERSPEED, SLOWDRIFT, SOUNDWAVE, ZUMKONG, and WINERACK.
Cisco Talos assesses APT 37 was responsible for the following six campaigns from January 2017 to January 2018: Golden Time, Evil New Year, Are You Happy, Free Milk, North Korean Human Rights, and Evil New Year 2018. The group has used spear-phishing emails containing malicious Hanword Document (HWP) files to execute a Remote Access Trojan (RAT) payload. The attack vector is similar to the KimJongRAT and BabyShark samples targeting US national security resources. Further, analysis of code reuse indicates a relationship between APT 37, DOGCALL (ROKRAT) and KimJongRAT.
Conclusion
Although the DPRK has been on a charm offensive and refrained from nuclear and missile testing, it has not refrained from cyber attacks. Also, while building up its conventional and nuclear missile capabilities, the DPRK has similarly built up its cyber threat arsenal. The mission of DPRK cyber threat assets is multi-faceted. DPRK cyber threat actors are engaged in targeting financial institutions, universities, research institutes, and other public and private entities. Any future negotiations with the DPRK must include their cyber capabilities, and the aforementioned institutions must maintain awareness of this space.
