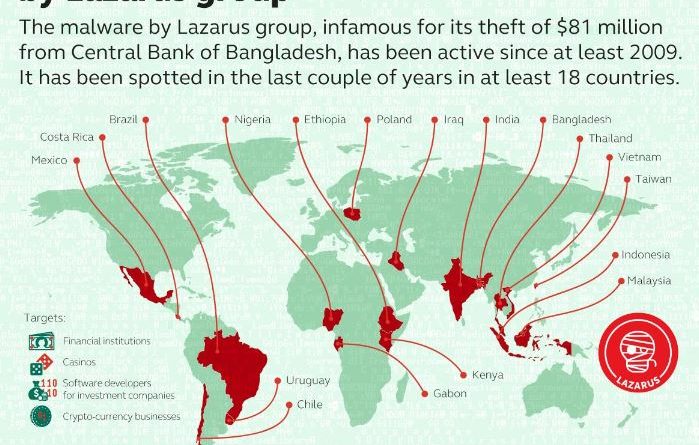
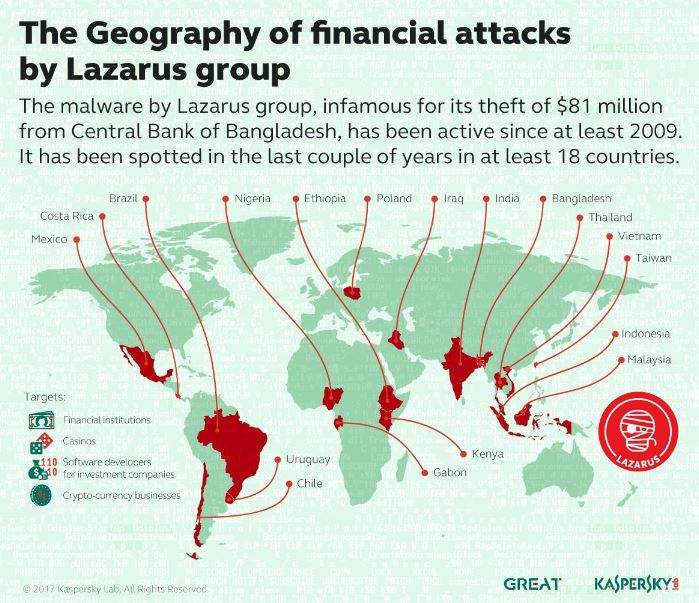
DPRK Sanctions and Cyber Attacks
In March I wrote about a DPRK threat actor targeting a US-based university and US-based think tank involved in DPRK denuclearization talks. I also wrote about some of the DPRK cyber threat actors involved in state-sponsored cyber activities. For this post, I plan to expand on target identification for one of the DPRK-backed threat actors and the goal of this group’s cyber operations.
2016 SWIFT Heist
First Stage
There was widespread reporting of a threat actor attempting to steal $951 million — successfully stealing $81 million — from Bangladesh’s Central Bank by sending payment instructions via the SWIFT system. The threat actor followed a 4 step approach to gain access to the SWIFT system. First, a webserver was compromised with an exploit and then used to install a backdoor on a company system. Next, after gaining a foothold in the network, the threat actor moved laterally deploying tools for privilege escalation. After network infiltration, the threat actor then began analyzing the company’s network and locating its critical assets. Finally, custom code was deployed on the SWIFT server (which was not segmented from the rest of the network) and the threat actors began sending payment instructions and covering their tracks for exfil.
Second Stage
The second stage of the bank heist relied on Rizal Commercial Banking Corporation’s Jupiter Street branch manager Maia Santos-Deguito and Eastern Hawaii Leisure Company president, Kam Sin Wong. The funds from the Bangladesh Central Bank passed through the Philippines-based RCBC, with the help of Santos-Deguito, to another Philippines-based account before ultimately transferring to Wong.
Attribution
BAE Systems’ investigation into the Bangladesh Central Bank heist revealed that it was part of a wider campaign. The BAE investigators noticed a unique file wipe-out function in the decompiled code and found a matching sample (msoutc.exe) uploaded from the US on 4 March 2016.
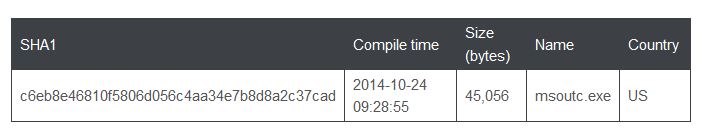
The unique wipe-out function, used by the malware to delete its configuration and log files after receiving a terminate command from the C2 server, is byte-to-byte identical to the wipe-out function called by the malware used in the attempted heist in Vietnam.

Vietnam’s Tien Phong Bank indicated it had interrupted an attempted heist using the same attack pattern as the Bangladesh heist. Symantec further indicated that this same malware sample was discovered in “targeted attacks against a bank in the Philippines.” Moreover, Symantec also reported on code sharing between the malware used in the Bangladesh attack, and other targeted attacks against banks in South East Asia.
Additionally, the msoutc.exe sample encrypts logged messages with a key that matches the SMB Worm Tool (SVCH0ST.EXE), used to target Sony Pictures Entertainment in 2014. Anomali Labs conducted deeper research based on Symantec’s attribution of the SWIFT activity to the Lazarus Group, and found additional malware samples using the unique wipe-out function. Further strengthening the attribution of financial services attacks to the Lazarus Group, Symantec discovered shared code in malware used in attacks against Polish banks with malware associated with Lazarus.
APT 38 | Bluenoroff
In 2017 Kaspersky released a reported titled Lazarus Under the Hood where they identify a Lazarus sub-group — Bluenoroff — responsible for attacks against financial institutions for profit. An in-depth report on APT 38 can be found by FireEye. Kaspersky identifies the tactics, techniques, and procedures used by the Bluenoroff sub-group and lists nine countries where Bluenoroff watering hole attacks have been observed: Mexico, Australia, Uruguay, Russia, Norway, India, Nigeria, Peru, and Poland. These watering hole attacks involved compromising a government website with an exploit containing whitelisted IP addresses associated with the group’s targets. Whenever one of the targets visited the compromised website, the exploit would be deployed on that system beginning the First Stage bank heist operations.
DPRK Sanctions
According to Hugh Griffiths’ UN PoE testimony before the House Foreign Affairs Asia, the Pacific, and Nonproliferation Subcommittee, the UN sanctions regime was transformed by 5 UN Security Council Resolutions adopted in response to DPRK nuclear and ballistic missile tests in 2016 and 2017. These sanctions, beginning with UNSCR 2270 on 2 March 2016, began to expand maritime and commodities sanctions culminating in the complete prohibition of DPRK exports of coal, iron, iron ore, lead, lead ore, and seafood with UNSCR 2371 on 5 September 2017. On 22 December 2017 UNSCR 2397 expanded Sectoral sanctions, prohibited DPRK selling or transferring of fishing rights, and forced UN member states to repatriate DPRK foreign workers within 24 months.
Despite the UN PoE report indicating the poor implementation of sanctions — especially in the maritime arena — these sanctions have clearly had the intended effect on the DPRK. There have been no further nuclear tests or ballistic missile launches since the latest 22 December 2017 sanctions, and the DPRK has attempted to attain sanctions relief through engagement with the Trump Administration. Further, the DPRK has enlisted the help of President Moon in lobbying for sanctions relief, underscoring the pressure these sanctions are placing on the DPRK. Interestingly, the DPRK’s cyber activities targeting the financial services sector also coincides with the expansion of the UN sanctions regime.
The DPRK has carried out at least five successful attacks against cryptocurrency exchanges in Asia between January 2017 and September 2018 resulting in a total loss of $571 million. Cyberattacks by the DPRK to illegally force the transfer of funds have become an important tool in the evasion of sanctions and have grown in sophistication and scale since 2016.
UN PoE 2019 Final report
Conclusion
If the DPRK and President Moon’s current push for sanctions relief is unsuccessful, I believe the APT 38/Bluenoroff group will continue to expand its cyber threat actions. Furthermore, DPRK interest in cryptocurrency exchanges may provide the Kim regime with a mechanism for illegal financial transactions with the PRC and Russia. At this time, the DPRK threat actors are targeting less developed nations’ financial services industries, and have not exploited the SWIFT system itself. However, the financial services sector in developed nations should continue to monitor IOCs associated with Bluenoroff malware samples and their TTPs.