New DPRK Malware Analysis Reports
CISA, FBI, and DOD released three new DPRK Malware Analysis Reports yesterday, and uploaded samples to VirusTotal. These joint reports were published on the three-year anniversary of the WannaCry campaign, which has been attributed to DPRK state-sponsored threat actors. This joint reporting follows the USG strategy of putting pressure on DPRK cyber theft activities by increasing public awareness of threat actor TTPs.
CopperHedge, TaintedScribe, and PebbleDash
CopperHedge is a variant of the Manuscrypt family of Remote Access Trojans (RATs), which is capable of running commands on the target system, gathering information about the system, and exfiltrating data from the system. Six variants of CopperHedge are presented in the MAR. While this family of malware has primarily targeted cryptocurrency exchanges and other entities associated with cryptocurrency, one of these variants was first observed in February 2018 in association with Operation GhostSecret, a global data reconnaissance campaign that targeted multiple industry sectors.
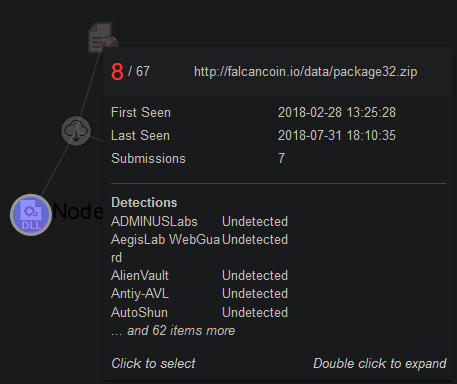
TaintedScribe and PebbleDash are beaconing implants that receive and execute attacker’s commands, and can further download, upload, delete, and execute files. TaintedScribe disguises itself as Microsoft Narrator and utilizes FakeSSL to obfuscate network communications.
PebbleDash also utilizes FakeSSL to obfuscate network communications and obfuscates API calls using a custom XOR algorithm.
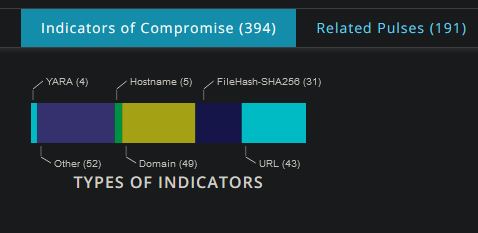
Indicators
The joint reporting provides IOCs in the STIX format. Additionally, the open source platform OTX provides IOCs available for download in multiple formats.